
LawPal security for AI contract review
Effective Date: 1 September 2025
Last Updated: 6 January 2026
Security at a glance
LawPal provides secure UK-focused AI contract review with 100% data residency in AWS Stockholm (eu-north-1), enterprise-grade AES-256 encryption, and a strict zero-data-training policy.
- Where is my data? Secure EU-based storage in AWS Stockholm (eu-north-1).
- Is my data used to train AI? No. User data is strictly isolated and never used for training.
- Is it UK compliant? Fully aligned with UK GDPR and ICO standards.
LawPal protects contract data during AI contract review with encryption, access controls, and monitoring designed for UK commercial workflows. This page summarises key security practices for procurement and due diligence, with contractual terms set out in the DPA and Terms.
LawPal is committed to safeguarding the confidentiality, integrity, and availability of all information entrusted to us. This Security Overview sets out the technical, organizational, and procedural measures adopted by LawPal in the provision of its services. It is intended to provide customers, partners, and regulators with transparency regarding our security posture, while serving as an assurance of our compliance with applicable data protection and information security obligations.
This overview applies to the LawPal platform used for AI contract review, AI contract analysis, and GDPR-compliant contract scanning by UK businesses. It is provided for transparency. Contractual commitments are set out in the DPA and Terms.
For privacy information, see the Privacy Policy. For procurement questions or residency requirements, contact Support or email security@lawpal.co.uk.
Secure AI contract analysis for UK businesses
LawPal is a contract analysis tool UK teams use for AI contract review and GDPR-compliant contract scanning. Our AES-256 encryption, AWS Stockholm (eu-north-1) data residency, and zero-data-training policy let you perform rapid AI contract analysis without compromising confidentiality or firm-wide data sovereignty.
Security controls such as role-based access control, multi-factor authentication, and secure audit trails are designed so legal and commercial teams can collaborate confidently, with evidence ready for client and procurement reviews.
1. Governance and Responsibility
Security is governed through documented policies and leadership accountability. Controls are designed to reduce risk across product, infrastructure, and operations.
1.1 Information Security Management System (ISMS)
LawPal maintains an internal information security framework modeled on ISO/IEC 27001 principles, covering policy enforcement, access control, operational security, and risk management.
1.2 Accountability
Responsibility for information security rests with senior management, supported by designated data protection and security roles responsible for day-to-day oversight.
2. Infrastructure and Data Residency for AI contract review
LawPal maintains 100% data residency in AWS Stockholm (eu-north-1). Customer content stays in this region, protected with encryption and strict access controls.
2.1 Hosting Environment
LawPal is hosted on Amazon Web Services (AWS) in the EU region eu-north-1 (Stockholm). This provides predictable data residency, strong physical security, and high availability within the region.
2.2 UK Data Residency
LawPal is built for UK workflows while maintaining EU-based data residency. Customer data remains in AWS eu-north-1 (Stockholm), and our security framework follows the UK Government's AI Cyber Security Code of Practice and the ICO's Guidance on AI and Data Protection to support UK GDPR expectations.
2.3 Physical Security
Our cloud providers employ industry-recognized safeguards including biometric access, 24/7 surveillance, and redundancy controls.
3. Data Protection for GDPR-compliant contract scanning
Contract and account data is protected with encryption in transit and at rest. Key management and backups are designed to preserve confidentiality and availability.
3.1 Encryption
- At Rest: All stored data is encrypted using AES-256 or stronger algorithms.
- In Transit: All network communications are protected using TLS 1.2 or higher.
This encryption enables rapid AI contract analysis while protecting confidentiality and supporting firm-wide data sovereignty.
3.2 Key Management
Encryption keys are managed using secure key vaults with restricted access, audit logging, and automated rotation.
3.3 Backups
Encrypted backups are performed regularly, replicated across multiple availability zones within AWS eu-north-1 (Stockholm), and subject to restoration testing.
4. Access Control
Access is restricted using role based controls, multi factor authentication, and least privilege. Logging and monitoring create an auditable trail for security review.
4.1 Authentication
Access to systems is restricted by role-based access control (RBAC) and enforced with multi-factor authentication (MFA).
4.2 Least Privilege Principle
Personnel are granted access strictly on a need-to-know basis. Administrative privileges are restricted and reviewed periodically.
4.3 Logging and Monitoring
All access is logged and monitored in real time, with automated alerts on anomalous activity.
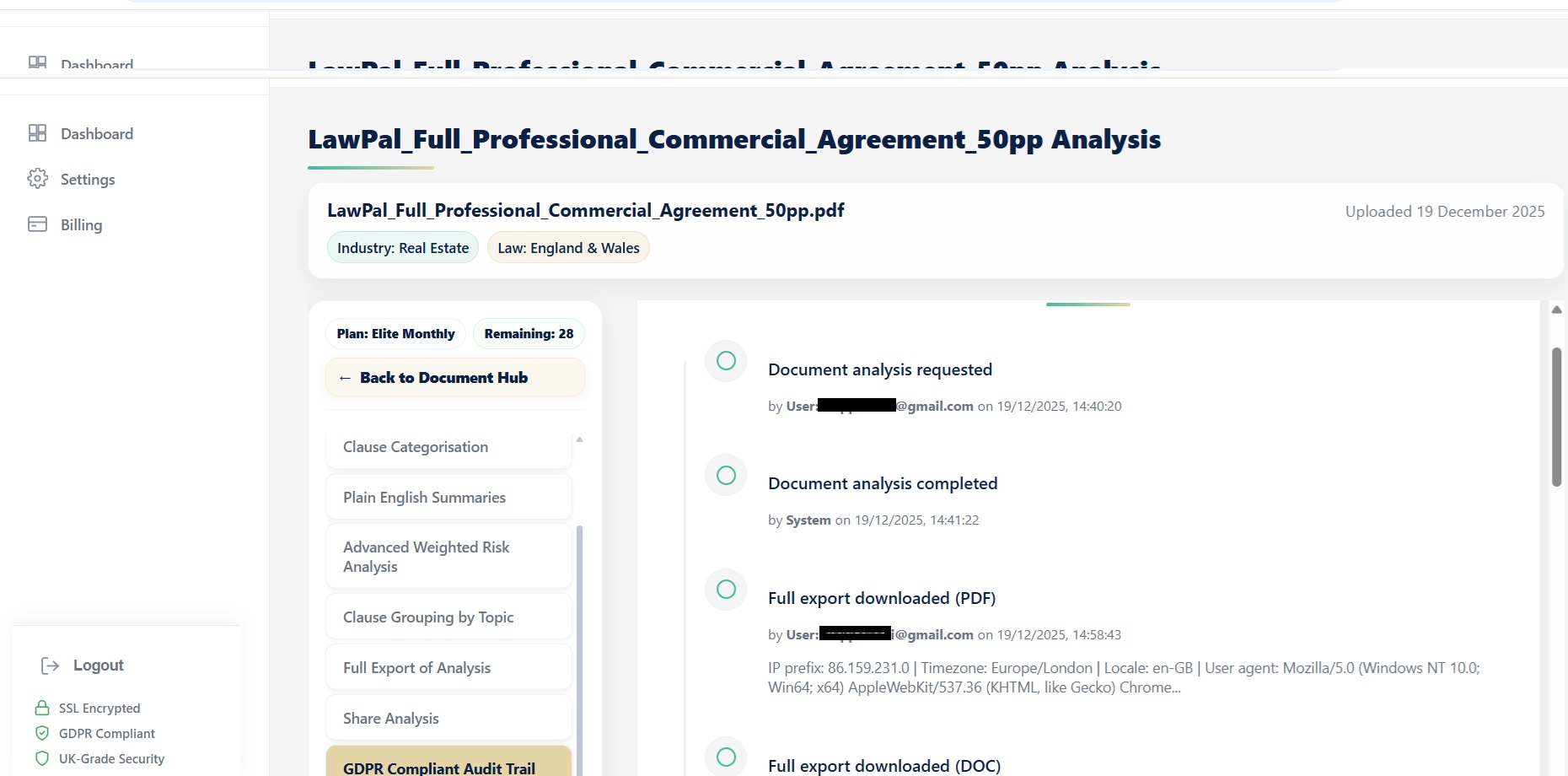
Audit evidence. Example Security Dashboard view demonstrating real-time audit trails and user activity logging, including downloadable history exports.
Audit logs and analysis history are encrypted with AES-256 at rest and protected with TLS 1.2+ in transit to support GDPR-compliant history management.
5. Monitoring and Incident Response
Continuous monitoring supports detection of suspicious activity. A documented incident response process governs investigation, containment, and legally required notifications.
5.1 Continuous Monitoring
LawPal employs continuous monitoring across infrastructure and applications. Logs are centrally collected, reviewed, and stored securely.
5.2 Incident Management
We maintain a documented incident response plan that includes identification, containment, eradication, and recovery phases.
5.3 Breach Notification
Where legally required, affected customers and supervisory authorities will be notified of a personal data breach without undue delay.
6. Compliance and Assurance
Controls are aligned to UK GDPR and the Data Protection Act 2018, with industry best practices for security assurance. Independent testing helps validate controls over time.
6.1 Regulatory Alignment
LawPal is designed to support UK GDPR and the Data Protection Act 2018 obligations. Our security framework follows the UK Government's AI Cyber Security Code of Practice and aligns with the ICO's Guidance on AI and Data Protection. Customers remain responsible for their own compliance and governance decisions.
6.2 Standards and Certifications
LawPal is actively aligning its security framework with ISO/IEC 27001 and SOC 2 Type II standards, with formal certification processes under consideration.
6.3 Third-Party Assessments
Independent audits and penetration tests are commissioned periodically to validate security controls.
7. Customer Rights and Data Processing
The DPA clarifies processing roles and customer instructions. Retention and deletion controls support data minimisation and governance obligations.
7.1 Data Processing Agreement (DPA)
A standard Data Processing Agreement is available to customers at lawpal.co.uk/dpa, outlining roles and responsibilities under applicable data protection laws.
7.2 Data Subject Rights
LawPal supports customer obligations with respect to rights of access, rectification, erasure, restriction, portability, and objection.
7.3 Data Retention and Deletion
Customer data is retained only as long as necessary for service provision and securely deleted thereafter.
8. Vendor and Sub-Processor Management
Vendors and sub-processors are assessed before onboarding and bound by written agreements. Sub-processor lists are available on request for procurement due diligence.
8.1 Due Diligence
All vendors and sub-processors undergo security and privacy due diligence before engagement.
8.2 Contracts
Written agreements are in place requiring sub-processors to implement appropriate technical and organizational measures.
8.3 Transparency
A list of current sub-processors is available upon request via Support.
9. Business Continuity and Resilience
Resilience controls are designed to keep the service available and recoverable. Backups, redundancy, and testing help reduce downtime risk.
9.1 Disaster Recovery
LawPal maintains a tested disaster recovery plan ensuring continuity of service in the event of system failure or natural disaster.
9.2 Redundancy
Infrastructure is designed with redundancy across power, network, and hardware layers.
9.3 Testing
Business continuity and recovery procedures are periodically tested and updated.
10. Updates to This Security Overview
This overview is updated as controls evolve and threats change. The effective date at the top indicates the most recent reviewed version.
This Security Overview may be updated from time to time to reflect evolving threats, technologies, or compliance obligations. Customers will be notified of material updates through appropriate channels.
11. Contact
Use this contact route for procurement questionnaires, security documentation requests, and vulnerability reporting. Include context and timelines to speed up triage.
Questions or concerns regarding security practices may be directed to:
LawPal Security Office
Email: security@lawpal.co.uk
Answer-first security FAQs for AI contract review
Answer-first FAQs written for how buyers and users actually search: AI contract review, contract analysis tool UK, and GDPR-compliant contract scanning. These are for transparency and do not override contractual terms.
How does LawPal keep contract data secure while performing AI contract review?
LawPal isolates customer data and protects contract content and analysis outputs with AES-256 encryption at rest and TLS 1.2+ in transit. Role-based access control, multi-factor authentication, and monitored audit logs help ensure only authorised users can access sensitive contract data while enabling rapid AI contract analysis.
Where is contract data stored for UK customers using LawPal?
All customer data is stored and processed with 100% data residency in AWS eu-north-1 (Stockholm). Encrypted backups are replicated across availability zones within the same region.
Is customer data used to train LawPal or third-party AI models?
No. LawPal applies a strict zero-data-training policy. Your uploads, extracted text, and analysis results are isolated per customer and are never used for model training.
How does LawPal support GDPR-compliant contract scanning and UK GDPR obligations?
LawPal is designed to support UK GDPR and the Data Protection Act 2018 obligations. Our security framework follows the UK Government's AI Cyber Security Code of Practice and aligns with the ICO's Guidance on AI and Data Protection, supporting procurement and governance expectations for AI contract review.
Which in-product security features support UK teams using LawPal as a contract analysis tool UK businesses rely on?
LawPal includes secure audit trails, encrypted history management, downloadable history exports, and role-based access control. These features provide evidence for internal reviews and client due diligence without compromising confidentiality.
Which sub-processors support the LawPal platform?
A current list of sub-processors and hosting details, including AWS Stockholm, is available on request via Support as part of procurement or vendor due diligence.
How do I report a security issue or request security documentation?
Email security@lawpal.co.uk with details of the issue or the documentation you need. Reports and requests are triaged and handled based on severity and customer timelines.